Cyber Security and Ethical Hacking Internship ...
- 15k Enrolled Learners
- Weekend/Weekday
- Live Class
We live in an age of information. Businesses these days are more digitally advanced than ever, and as technology improves, organizations’ security postures must be enhanced as well. Now, with many devices communicating with each other over wired, wireless, or cellular networks, network security is an important concept. In this article, we will explore what is network security and its key features.
Network security is the process of taking preventative measures to protect the underlying networking infrastructure from unauthorized access, misuse, malfunction, modification, destruction or improper disclosure.
The Internet has undoubtedly become a huge part of our lives. Many people in today’s generation rely on the Internet for many of their professional, social and personal activities. But are you sure your network is secure?
There are many people who attempt to damage our Internet-connected computers, violate our privacy and make it impossible to the Internet services. Given the frequency and variety of existing attacks as well as the threat of new and more destructive future attacks, network security has become a central topic in the field of cybersecurity. Implementing network security measures allows computers, users and programs to perform their permitted critical functions within a secure environment.
To become a trusted cybersecurity professional enroll now in the CISSP Certification and get certified.
We must ensure that the passwords are Strong and Complex everywhere- within the network too, not just on individual computers within an org. These passwords cannot be simple , default and easily guessable ones. This simple step can go a long way toward securing your networks.
Information security performs key roles such as:
The above mentioned topics are covered in detail later on in this blog.
Go through our CEH Certification Course to explore more about ethical hacking. This course will teach you the most current hacking techniques, tools and methods that hackers use.
Now that we know what network security is, let’s take a look at two major categories of network attacks.
A network attack can be defined as any method, process, or means used to maliciously attempt to compromise network security. Network security is the process of preventing network attacks across a given network infrastructure, but the techniques and methods used by the attacker further distinguish whether the attack is an active cyber attack, a passive type attack, or some combination of the two.
Let’s consider a simple network attack example to understand the difference between active and passive attack.
Related Post Aircrack without Wi-Fi card
An active attack is a network exploit in which attacker attempts to make changes to data on the target or data en route to the target.
Meet Alice and Bob. Alice wants to communicate to Bob but distance is a problem. So, Alice sends an electronic mail to Bob via a network which is not secure against attacks. There is another person, Tom, who is on the same network as Alice and Bob. Now, as the data flow is open to everyone on that network, Tom alters some portion of an authorized message to produce an unauthorized effect. For example, a message meaning “Allow BOB to read confidential file X” is modified as “Allow Smith to read confidential file X”.
Active network attacks are often aggressive, blatant attacks that victims immediately become aware of when they occur. Active attacks are highly malicious in nature, often locking out users, destroying memory or files, or forcefully gaining access to a targeted system or network.
Related Post Brute force protection with Redis
A passive attack is a network attack in which a system is monitored and sometimes scanned for open ports and vulnerabilities, but does not affect system resources.
Let’s consider the example we saw earlier:
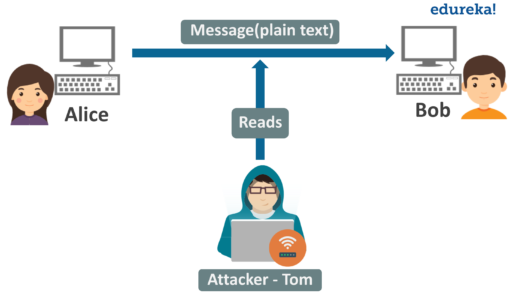
Alice sends an electronic mail to Bob via a network which is not secure against attacks. Tom, who is on the same network as Alice and Bob, monitors the data transfer that is taking place between Alice and Bob. Suppose, Alice sends some sensitive information like bank account details to Bob as plain text. Tom can easily access the data and use the data for malicious purposes.
So, the purpose of the passive attack is to gain access to the computer system or network and to collect data without detection.
So, network security includes implementing different hardware and software techniques necessary to guard underlying network architecture. With the proper network security in place, you can detect emerging threats before they infiltrate your network and compromise your data.
Explore various domains of Cybersecurity through this Cyber Security Internship, including Network Security, Cryptography and Web Application Hacking.
Related Post CSRF attack example
There are many components to a network security system that work together to improve your security posture. The most common network security components are discussed below.
To keep out potential attackers, you should be able to block unauthorized users and devices from accessing your network. Users that are permitted network access should only be able to work with the set of resources for which they’ve been authorized.
Application security includes the hardware, software, and processes that can be used to track and lock down application vulnerabilities that attackers can use to infiltrate your network.
A firewall is a device or service that acts as a gatekeeper, deciding what enters and exits the network. They use a set of defined rules to allow or block traffic. A firewall can be hardware, software, or both.
A virtual private network encrypts the connection from an endpoint to a network, often over the Internet. This way it authenticates the communication between a device and a secure network, creating a secure, encrypted “tunnel” across the open internet.
You should know what normal network behavior looks like so that you can spot anomalies or network breaches as they happen. Behavioral analytics tools automatically identify activities that deviate from the norm.
Wireless networks are not as secure as wired ones. Cybercriminals are increasingly targeting mobile devices and apps. So, you need to control which devices can access your network.
These systems scan network traffic to identify and block attacks, often by correlating network activity signatures with databases of known attack techniques.
So, these are some ways of implementing network security. Apart from these, you’ll need a variety of software and hardware tools in your toolkit to ensure network security, those are:
Network security is essential for overall cybersecurity because network is a significant line of defense against external attack. Given that, virtually all data and applications are connected to the network, robust network security protects against data breaches.
Read Related Post Hiding information from netstat
With the widely reported success of popular cyberattacks, like WannaCry and Adylkuzz, companies are paying more than ever to land highly qualified cybersecurity professionals to secure their most vulnerable assets. Network security analyst and network security engineer are listed as two of the highest paid cybersecurity jobs. While network security engineer is more likely to be building out security systems, a network security analyst is more likely to be tasked with scanning the network for plausible vulnerabilities. Both the positions earn an average between $90,000 and $150,000.
Related Post Using DNS DIG commands in Python scripts
If you wish to learn cybersecurity and build a colorful career in cybersecurity, then check out our Cyber Security Course which comes with instructor-led live training and real-life project experience. This training will help you understand cybersecurity in depth and help you achieve mastery over the subject.
You can also take a look at our newly launched course on CompTIA Security+ Certification Course which is a first-of-a-kind official partnership between Edureka & CompTIA Security+. It offers you a chance to earn a global certification that focuses on core cybersecurity skills which are indispensable for security and network administrators.
Learn Cybersecurity the right way with Edureka’s masters in cyber security program and defend the world’s biggest companies from phishers, hackers and cyber attacks.
Got a question for us? Please mention it in the comments section of “What is Network Security?” and we will get back to you.
 Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUP
Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUPedureka.co
Hi,
Thank you for this wonderful blog on Networking security This is a very nice one and gives in-depth information. I am really happy with the quality and presentation of the article. I’d really like to help appreciate it with the efforts you get with writing this post. Thanks for sharing.